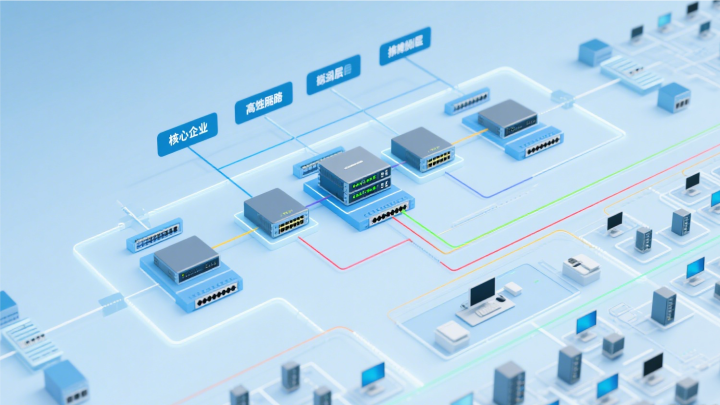
Enterprise LAN security access control system project
Enterprise LAN Security Access Control System Project With the continuous expansion of enterprise scale and increasing personnel mobility, security risks faced by enterprises have also grown. To ensure the safety of corporate assets and personnel, the enterprise LAN security access control system project has emerged as a crucial defense line in enterprise safety management.
1. System type and characteristics

The password access control system operates by requiring correct passwords to open doors. Its advantages include low cost and eliminating the need for additional cards or devices. However, it has notable drawbacks: passwords are easily leaked, and password management is cumbersome. Once compromised, security becomes significantly compromised. This system is primarily suitable for small businesses with minimal security requirements, such as small offices and warehouses.
The card-swiping access control system enables entry through a swipe of a stored card containing user information. The system verifies access permissions by scanning the card's data. Its advantages include user-friendly operation, portable cards, and enhanced security compared to traditional password-based systems. However, it has drawbacks such as increased risk of card loss or misuse, along with the need for regular management and maintenance. This system is particularly suitable for small-to-medium enterprises and office buildings where personnel are relatively fixed.

The Biometric Access Control System utilizes human biometric features such as fingerprints, facial recognition, and iris scanning for identity verification to enable access control. Its advantages include exceptional security due to the unique and non-replicable nature of biometric data, which makes it difficult to forge or misuse. However, it has drawbacks including higher costs and more complex installation and maintenance requirements. This system is particularly suitable for enterprises with stringent security demands, such as financial institutions, research organizations, and large state-owned enterprises.
2. System composition
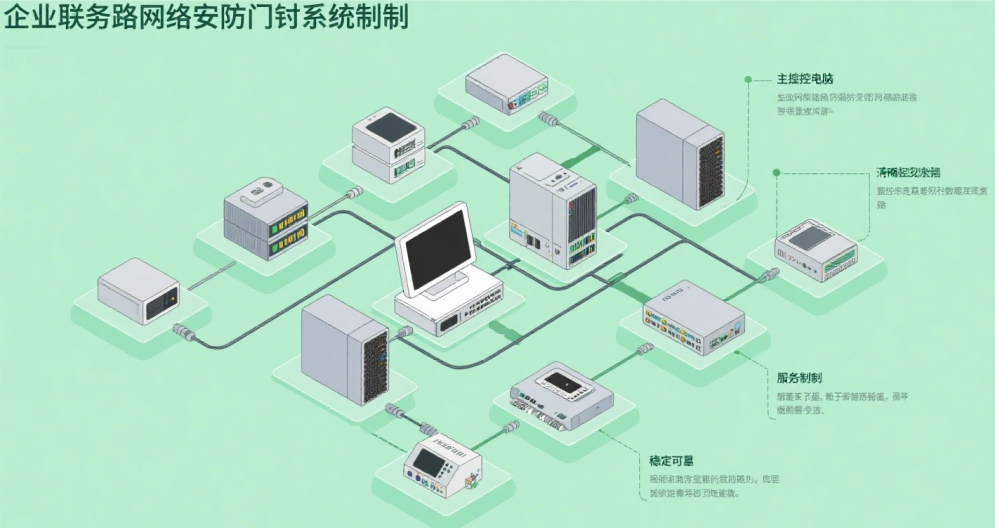
(1) Identification Unit The identification unit serves as the "eyes" of an access control system, responsible for verifying personnel identities. It can be implemented through devices such as password entry pads, card readers, fingerprint scanners, or facial recognition cameras. When individuals attempt to enter a facility, they input or present their identity information to the unit, which then collects and performs preliminary processing of the data.
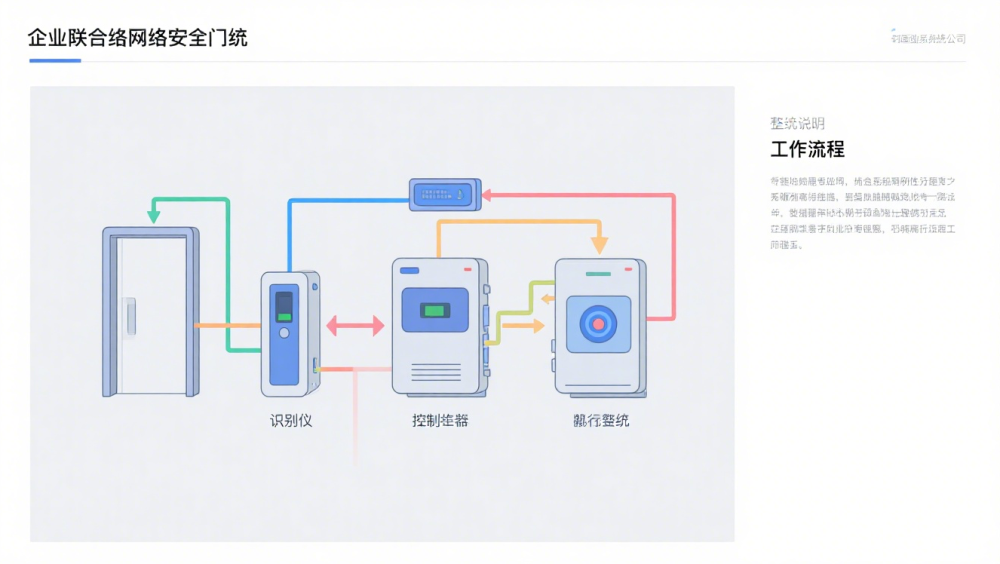
(2) Control Unit The control unit serves as the "brain" of the access control system. It receives information from the recognition unit and evaluates it according to predefined permission rules. If the identity information meets the authorization requirements, the control unit will issue an opening command to the execution unit; otherwise, it will reject the request and may trigger an alarm signal. Typically composed of an access controller, the control unit can also connect to a corporate local area network (LAN) to enable data upload and remote control.
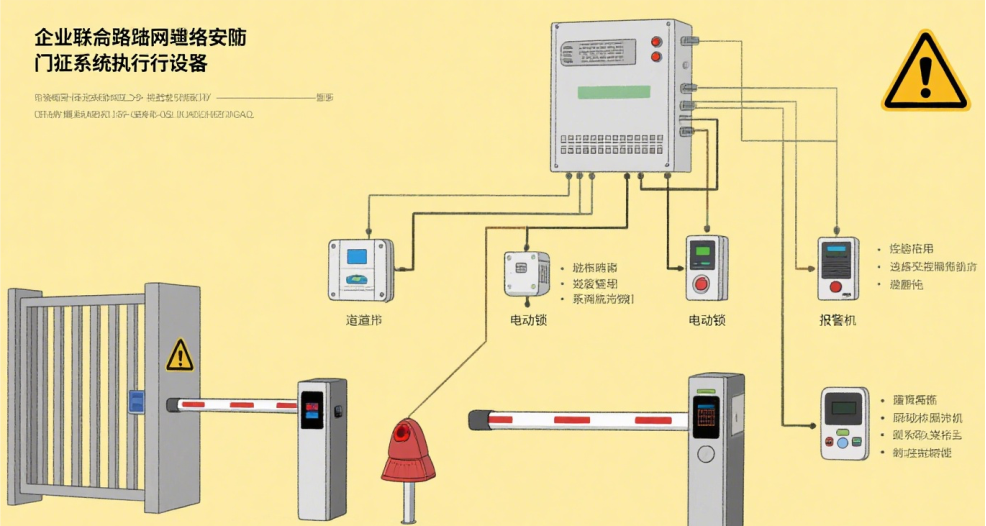
(3) Execution Unit The execution unit serves as the "hands and feet" of the access control system, responsible for executing commands issued by the control unit. It primarily includes devices such as electric locks and door sensors. When receiving an opening command from the control unit, the electric lock opens to allow entry. If a person enters or fails to enter within the set time limit, the lock automatically closes. Door sensors detect door status changes and relay this information back to the control unit. These units work in coordination: the recognition unit collects data and transmits it to the control unit, which then issues instructions to the execution unit. The execution unit executes these commands to collectively achieve the access control function.
3. Main functions
(1) Personnel Access Management The system can set different access rights for different personnel, such as some personnel can only enter specific areas during specific periods of time, while others can freely enter and exit all areas. Through strict control of personnel access, the system can prevent irrelevant personnel from entering the enterprise and ensure enterprise security.

(2) Real-time monitoring The system can monitor the opening and closing status of access control and the entry and exit of personnel in real time, and transmit relevant information to the monitoring center in real time. Managers can view the situation of each access control point through the screen of the monitoring center in real time, and take corresponding measures in time when abnormal situations are found.

(3) Record Inquiry The system automatically records all personnel's entry and exit information, including time, identity, location, etc. These records can be queried by management at any time, providing a strong basis for enterprise safety management. In case of security incidents, relevant personnel can be quickly traced through the records.

(4) Alarm Function When abnormal situations occur, such as unauthorized personnel attempting to forcibly enter or access control being damaged, the system will automatically send out alarm signals to remind management personnel to deal with them in time. The alarm signals can be sound alarms, light alarms, or transmitted to management personnel's mobile phones and other devices through the network.
-
fibre-optical
Jul 22, 2025
-
Classified by control technology
Jul 22, 2025
-
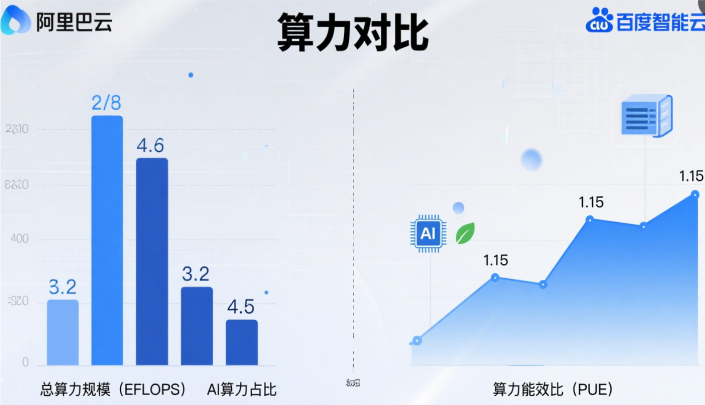
Aliyun VS Baidu Cloud
Jul 19, 2025
-
Smart factory network cabling
Jul 19, 2025
-
Full analysis of wiring test tools
Jul 19, 2025
-
Enterprise network cabling
Jul 19, 2025
-
Can you do smart control without the Internet
Jul 19, 2025
-
Principle of whole house intelligent control
Jul 18, 2025
-
Specifications and functions of light modules
Jul 18, 2025
-
Fiber optic engineering
Jul 18, 2025
-
Common classifications and their specific types:
Jul 18, 2025
-
Parking fee system
Jul 14, 2025
-
Video face recognition big data system
Jul 14, 2025
-
Starlink is a low-orbit satellite launched by SpaceX
Jul 14, 2025
-
5G base station project
Jul 14, 2025
-
5G and Starlink overview
Jul 14, 2025
-
Internet Data Center (IDC)
Jul 11, 2025
-
Enterprise LAN solutions
Jul 10, 2025
-
Video transmission theory
Jul 10, 2025
-
Patented technology and marked RJ45 crystal head
Jul 10, 2025
-
Advantages and disadvantages of intelligent control
Nov 30, 2024
-
Video Streaming Data Center
Nov 30, 2024
-
Computer Centre
Nov 30, 2024